Fully disabling Network Discovery in Windows 10 using Group Policy
To properly disable Network Discovery in Windows 10 in a way that the user cannot easily re-enable we must create some firewall rules and prevent some services from running on start-up. We can do both things using Group Policy.
Firewall Rules
Create a new Group Policy or use an existing one that takes effect on computer objects.
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > Windows Firewall with Advanced Security.
- Inside the Inbound Rules node, right click and choose New Rule.
- On Rule Type, select Predefined and choose Network Discovery then click Next.
- You will be presented with a long list of rules, many of which are duplicates because of the Profile they belong to; Public, Domain, Private.
- Select only the following rules, it does not matter which profile as we will change it later.
- Network Discovery (LLMNR-UDP-In)
- Network Discovery (NB-Datagram-In)
- Network Discovery (NB-Name-In)
- Network Discovery (Pub-WSD-In)
- Network Discovery (SSDP-In)
- Next, choose Block the connection and click Finish.
- We will now make some changes to those rules.
- First, select Network Discovery (NB-Datagram-In) and go to its properties.
- On the General tab, select the Allow the connection radio button.
- Next on the Scope tab, under Remote IP address, select the These IP addresses: radio button and then click Add…
- In the new window, select the Predefined set of computers: radio button and choose Local subnet from the drop-down list.
- Next on the Advanced tab, make sure that the check boxes next to Domain, Private and Public are all checked.
- Click on Apply, and close the properties window.
- On the other 4 inbound rules repeat steps 10 - 13.
Your inbound firewall rules should look like this:
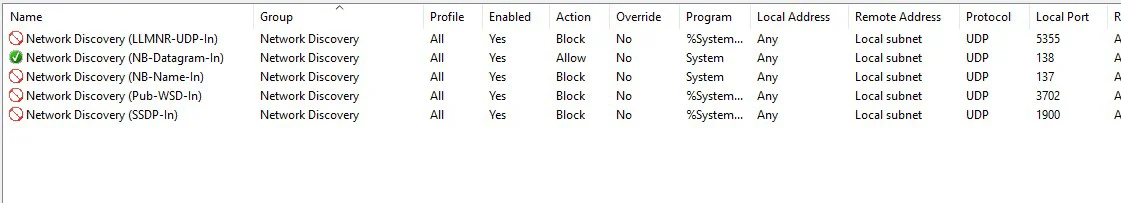
We are now going to repeat the steps above for the outbound rules.
- Inside the Outbound Rules node, right click and choose New Rule.
- On Rule Type, select Predefined and choose Network Discovery then click Next.
- You will be presented with a long list of rules, many of which are duplicates because some the Profile they belong to e.g. Public, Domain, Private.
- Select only the following rules, it does not matter which profile as we will change it later.
- Network Discovery (LLMNR-UDP-Out)
- Network Discovery (NB-Datagram-Out)
- Network Discovery (NB-Name-Out)
- Network Discovery (Pub-WSD-Out)
- Network Discovery (SSDP-Out)
- Next, choose Block the connection and click Finish.
- We will now make some changes to those rules.
- First, select Network Discovery (NB-Datagram-Out) and go to its properties.
- On the General tab, select the Allow the connection radio button.
- Next on the Scope tab, under Remote IP address, select the These IP addresses: radio button and then click Add…
- In the new window, select the Predefined set of computers: radio button and choose Local subnet from the drop-down list.
- Next on the Advanced tab, make sure that the check boxes next to Domain, Private and Public are all checked.
- Click on Apply, and close the properties window.
- On the other 4 inbound rules repeat steps 9 - 12.
Your outbound firewall rules should look like this:
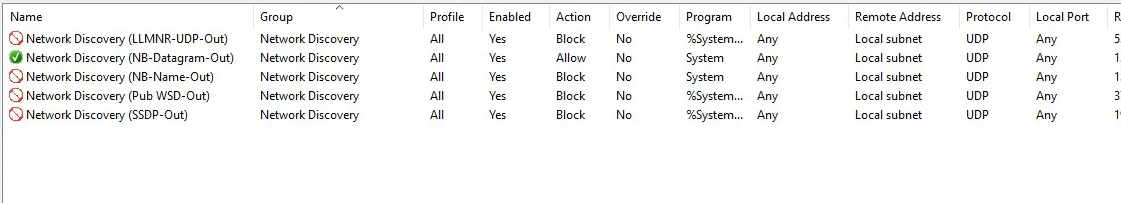
System Services
Now we are going to configure the Group Policy to disable some system services.
- Go to Computer Configuration > Policies > Windows Settings > Security Settings > System Services.
- Select the Function Discovery Provider Host service and go to it properties page.
- Select Define this policy setting, choose Disabled and then click on Apply and close the properties window.
- Repeat the above steps for the following services:
- Function Discovery Resource Publication
- Link-Layer Topology Discovery Mapper
- SSDP Discovery
- UPnP Device Host
The Group Policy is now configured. Link it to an OU or OU’s that contain computer objects and run gpupdate or restart the computers. Network Discovery will now be disabled and even if a user enabled it in the Network and Sharing Center it will remain disabled.
Support My Work
If you would like to support me, please check out the link below.
If you have any questions or comments, please leave them below.
-Mike